🎯Strategic IT Leadership Framework
This comprehensive IT Strategy Roadmap serves as your guide for aligning technology initiatives with business objectives in today's rapidly evolving digital landscape. Beyond being a technical blueprint, this is a critical enabler of organizational growth, efficiency, and competitive advantage.
Key Focus: Structured approach to developing, implementing, and governing IT strategies that are granular, adaptable, and forward-looking - from current state assessment to emerging technology integration.
📋1. Executive Summary
This IT Strategy Roadmap serves as a comprehensive guide for organizations seeking to align their technology initiatives with overarching business objectives. In today's rapidly evolving digital landscape, a well-defined IT strategy is not merely a technical blueprint but a critical enabler of organizational growth, efficiency, and competitive advantage. This roadmap outlines a structured approach to developing, implementing, and governing IT strategies that are granular, adaptable, and forward-looking. It addresses key components from current state assessment and future visioning to emerging technology integration and robust governance frameworks.
The primary objective of this roadmap is to provide actionable insights and methodologies for IT leaders and stakeholders to navigate the complexities of technology planning and implementation. By leveraging established frameworks and incorporating insights from current industry trends, this document aims to facilitate informed decision-making, optimize resource allocation, and foster a culture of continuous technological innovation. The successful execution of this roadmap will empower organizations to harness the full potential of their IT investments, drive digital transformation, and achieve sustainable business outcomes.
🌐2. Introduction and Context
Information Technology (IT) has transcended its traditional role as a support function to become an indispensable strategic asset for modern enterprises. An effective IT strategy is the cornerstone of digital success, dictating how technology resources are deployed to meet business demands, enhance operational efficiency, and create new value propositions. This section establishes the foundational understanding of IT strategy within the broader organizational context, emphasizing its critical importance in an era characterized by rapid technological advancements and dynamic market conditions.
Definition of IT Strategy and its Importance
An IT strategy is a detailed plan that outlines how technology will be utilized to support and achieve an organization's business goals [1]. It is a proactive approach that ensures technology investments are not isolated decisions but are intricately woven into the fabric of the overall business strategy. The importance of a robust IT strategy cannot be overstated, as it:
- Aligns IT with Business Objectives: Ensures that all technology initiatives directly contribute to the achievement of organizational goals, preventing misaligned investments and maximizing return on IT expenditure.
- Enhances Decision-Making: Provides a clear framework for prioritizing IT projects, allocating resources, and making informed choices regarding technology adoption and infrastructure development.
- Drives Innovation: Fosters an environment where emerging technologies can be strategically evaluated and integrated, enabling organizations to stay competitive and responsive to market shifts.
- Optimizes Operations: Streamlines business processes, improves efficiency, and reduces operational costs through the strategic application of technology.
- Manages Risk: Identifies and mitigates technology-related risks, including cybersecurity threats, data breaches, and system failures, thereby safeguarding organizational assets and reputation.
Current Business Environment and Technology Landscape
Today's business environment is characterized by unprecedented volatility, uncertainty, complexity, and ambiguity (VUCA). Digital disruption, evolving customer expectations, and the imperative for agility demand that organizations continuously adapt their strategies. The technology landscape is equally dynamic, marked by the pervasive influence of:
- Cloud Computing: Offering scalable, flexible, and cost-effective infrastructure solutions that enable rapid deployment and innovation.
- Artificial Intelligence (AI) and Machine Learning (ML): Revolutionizing data analysis, automation, and decision-making across various business functions.
- Cybersecurity Threats: Increasing in sophistication and frequency, necessitating robust defense mechanisms and proactive risk management.
- Data Analytics and Big Data: Providing actionable insights from vast datasets, driving personalized customer experiences and optimized operational performance.
- Internet of Things (IoT): Connecting physical devices and enabling real-time data collection and automation.
- Automation and Robotics: Transforming workflows and enhancing productivity in both manufacturing and service industries.
These technological advancements present both immense opportunities and significant challenges. Organizations must strategically leverage these technologies to maintain relevance, foster innovation, and achieve sustainable growth.
Alignment with Organizational Goals and Vision
The fundamental principle underlying any successful IT strategy is its unwavering alignment with the organization's overarching goals and vision. An IT strategy should not exist in isolation but rather serve as a direct enabler of the business strategy. This alignment ensures that IT investments are purposeful, contribute to strategic outcomes, and are perceived as value-adding rather than merely cost centers. Key aspects of this alignment include:
- Shared Vision: IT leadership and business leadership must collaborate to articulate a unified vision for how technology will support and drive the organization's future state.
- Goal Synchronization: Specific IT objectives must be directly traceable to broader business objectives, ensuring that technology initiatives contribute to measurable business outcomes.
- Strategic Prioritization: IT projects and initiatives should be prioritized based on their potential impact on strategic business goals, ensuring that resources are allocated to the most critical areas.
Stakeholder Identification and Engagement
Effective IT strategy development and implementation necessitate active engagement from a diverse group of stakeholders. Identifying and involving these individuals from the outset is crucial for gathering comprehensive requirements, fostering buy-in, and ensuring the strategy addresses the needs of all relevant parties. Key stakeholders typically include:
- Executive Leadership: (CEO, CFO, COO) Provide strategic direction, approve major investments, and champion the IT strategy across the organization.
- Business Unit Leaders: Represent the specific needs and priorities of their respective departments, ensuring the IT strategy supports their operational and strategic objectives.
- IT Leadership and Staff: (CIO, CTO, IT Managers, Architects, Engineers) Are responsible for the technical feasibility, design, and implementation of the IT strategy.
- End-Users: Provide valuable insights into the usability and effectiveness of current systems and inform requirements for future solutions.
- Customers: Their evolving needs and expectations often drive technological innovation and service delivery improvements.
- Vendors and Partners: External entities that provide technology solutions, services, or strategic alliances.
Engaging these stakeholders through workshops, interviews, and regular communication channels ensures that the IT strategy is holistic, well-informed, and widely supported, paving the way for successful execution.
References
[1] Electric AI. (2023, April 6). What is an IT Strategy? Framework & Examples. Retrieved from https://www.electric.ai/blog/guide-to-it-strategy
🏗️3. Strategic Framework Foundation
A robust IT strategy is built upon a solid foundational framework that defines its essential elements, their interrelationships, and how they contribute to achieving business objectives. This section delves into the core components of an IT strategy framework, emphasizing its role in providing structure, ensuring consistency, and facilitating effective decision-making within the technology landscape.
IT Strategy Framework Components and Relationships
An IT Strategy Framework provides the logical and conceptual underpinnings for developing a comprehensive IT strategy. It specifies the variables and elements necessary to solve the "IT enabled or driven creation of business value" puzzle [2]. While various frameworks exist, a typical IT strategy framework includes the following key components and their interrelationships:
- Business Objectives: These are the overarching goals of the organization that the IT strategy aims to support. The IT strategy must be directly derived from and aligned with these objectives, ensuring that technology investments contribute to measurable business outcomes.
- Current State Assessment: This involves a thorough analysis of the organization's existing technology infrastructure, applications, processes, and capabilities. Understanding the current state is crucial for identifying strengths, weaknesses, and areas requiring improvement or modernization.
- Future State Vision: This component defines the desired future state of technology within the organization, outlining how IT will evolve to meet future business needs and leverage emerging opportunities. It provides a clear target for IT initiatives.
- IT Initiatives: These are specific projects, programs, or actions designed to bridge the gap between the current state and the future state vision. They represent the concrete steps required to implement the IT strategy.
- Prioritization: Given limited resources, IT initiatives must be prioritized based on factors such as their strategic impact, feasibility, cost, and alignment with business objectives. This ensures that the most critical initiatives receive the necessary attention and resources.
- Implementation Plan: A detailed plan for executing the IT initiatives, including timelines, budgets, resource requirements, and key milestones. This translates the strategic vision into actionable steps.
- Governance: Establishing clear governance processes is essential to ensure ongoing alignment between IT and business goals, manage risks, monitor progress, and make informed decisions throughout the strategy lifecycle.
These components are interconnected and interdependent. For instance, the Current State Assessment informs the Future State Vision, which then drives the identification and prioritization of IT Initiatives. Effective Governance ensures that all components remain aligned with Business Objectives throughout the implementation process.
Essential Elements of Effective IT Strategy
Beyond the structural components of a framework, an effective IT strategy embodies several essential elements that contribute to its success and impact:
- Alignment with Business Strategy: This is paramount. The IT strategy must be a direct enabler of the overall business strategy, ensuring that technology investments and initiatives directly support and drive the organization's strategic goals [1].
- Clear Vision and Mission: The IT strategy should articulate a clear vision for how technology will contribute to the organization's future and a mission statement that defines its purpose and scope. These statements serve as guiding principles for all IT decisions.
- Measurable Objectives: Strategic IT objectives should be specific, measurable, achievable, relevant, and time-bound (SMART). This allows for effective tracking of progress and evaluation of success.
- Adaptability and Agility: In a rapidly changing technological landscape, an effective IT strategy must be flexible and adaptable, capable of responding to new opportunities, market shifts, and unforeseen challenges.
- Risk Management Integration: Proactive identification, assessment, and mitigation of IT-related risks (e.g., cybersecurity, data privacy, system failures) are crucial for safeguarding organizational assets and ensuring business continuity.
- Innovation Focus: The strategy should foster a culture of innovation, encouraging the exploration and adoption of emerging technologies that can provide a competitive advantage or improve operational efficiency.
- Talent and Capabilities: Recognizing that people are central to technology success, an effective IT strategy addresses the need for skilled talent, continuous learning, and the development of internal IT capabilities.
- Financial Prudence: The strategy must include sound financial planning, ensuring that IT investments are justified, cost-effective, and deliver a positive return on investment.
Framework Selection Criteria and Rationale
Choosing the right IT strategy framework depends on an organization's specific needs, industry, size, and strategic objectives. While there is no one-size-fits-all solution, several criteria can guide the selection process:
- Relevance to Business Context: The chosen framework should align with the organization's industry, regulatory environment, and unique business challenges.
- Scalability and Flexibility: The framework should be adaptable to the organization's growth and evolving technological landscape.
- Ease of Understanding and Implementation: A practical framework should be comprehensible to both IT and business stakeholders, facilitating collaboration and adoption.
- Comprehensive Coverage: The framework should address all critical aspects of IT strategy, from planning and execution to governance and performance measurement.
- Availability of Tools and Resources: The existence of supporting tools, methodologies, and best practices can significantly aid in the framework's implementation.
For this roadmap, a hybrid approach drawing from established frameworks like those discussed in the research (e.g., elements of Balanced Scorecard for performance, SWOT for assessment, and a phased implementation approach) will be utilized to provide a comprehensive yet flexible guide. The rationale is to leverage the strengths of various proven methodologies to create a tailored and effective IT strategy roadmap.
Integration with Business Strategy
The seamless integration of IT strategy with overall business strategy is not merely a best practice but a fundamental requirement for success. This integration ensures that IT is viewed as a strategic partner rather than a cost center. Key aspects of this integration include:
- Joint Planning: IT and business leaders must collaborate from the initial stages of strategic planning, ensuring that technology considerations are embedded in business objectives.
- Shared Metrics: Performance metrics for IT initiatives should be directly linked to business outcomes, demonstrating the tangible value IT brings to the organization.
- Cross-Functional Teams: Establishing teams that include both IT and business representatives fosters mutual understanding, facilitates communication, and ensures that technology solutions meet business needs.
- Business Case Development: Every major IT investment should be supported by a clear business case that articulates its strategic alignment, expected benefits, and return on investment.
- Continuous Dialogue: Regular communication and feedback loops between IT and business functions are essential to adapt the IT strategy as business priorities evolve.
By fostering deep integration, organizations can ensure that their IT strategy is not just a technical plan, but a powerful engine driving business innovation and competitive advantage.
References
[1] Electric AI. (2023, April 6). What is an IT Strategy? Framework & Examples. Retrieved from https://www.electric.ai/blog/guide-to-it-strategy [2] CIO Wiki. (2023, August 11). IT Strategy Framework. Retrieved from https://cio-wiki.org/wiki/IT_Strategy_Framework
📊4. Current State Assessment
A thorough current state assessment is a critical first step in developing an effective IT strategy. It provides a baseline understanding of the organization's existing technology landscape, capabilities, and challenges. This comprehensive evaluation allows for the identification of strengths to leverage, weaknesses to address, opportunities to pursue, and threats to mitigate. Without a clear picture of the current state, any future-state vision or strategic initiative would be built on an unstable foundation.
IT Infrastructure and Systems Evaluation
This evaluation involves a detailed inventory and analysis of all hardware, software, networks, and data systems currently in use. The objective is to understand their current performance, scalability, reliability, and security. Key areas of focus include:
- Hardware Infrastructure: Servers, storage, networking equipment, end-user devices (desktops, laptops, mobile devices). Assess age, capacity, performance, and maintenance status.
- Software Applications: Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), Human Resources (HR) systems, custom applications, and productivity tools. Evaluate their functionality, integration, and user adoption.
- Network Infrastructure: Local Area Networks (LAN), Wide Area Networks (WAN), wireless networks, and internet connectivity. Assess bandwidth, latency, security, and resilience.
- Data Management: Databases, data warehouses, data lakes, and data governance practices. Evaluate data quality, accessibility, security, and compliance.
- Cloud Services: Public, private, or hybrid cloud deployments. Assess utilization, cost-effectiveness, security, and compliance with organizational policies.
The evaluation should identify any legacy systems that are costly to maintain, pose security risks, or hinder agility. It should also highlight systems that are performing well and can be leveraged for future growth.
Technology Capability Assessment
Beyond the physical infrastructure, a capability assessment focuses on the human and process aspects of IT. This involves evaluating the skills, processes, and organizational structures within the IT department and across the organization that enable or hinder technology utilization. Key areas include:
- IT Staffing and Skills: Assess the current skill sets of IT personnel, identify any skill gaps relative to current and future technology needs, and evaluate staffing levels and organizational structure.
- IT Processes and Methodologies: Review IT Service Management (ITSM), project management, software development lifecycle (SDLC), and operational processes. Evaluate their efficiency, effectiveness, and adherence to best practices (e.g., ITIL, COBIT).
- Data Analytics Capabilities: Assess the organization's ability to collect, process, analyze, and derive insights from data. This includes tools, expertise, and data governance.
- Cybersecurity Capabilities: Evaluate the organization's ability to prevent, detect, respond to, and recover from cyber threats. This includes security policies, technologies, and incident response plans.
- Innovation Capacity: Assess the organization's ability to identify, evaluate, and adopt new technologies and innovative solutions.
Performance Benchmarking
Benchmarking involves comparing the organization's IT performance against industry standards, best practices, and competitors. This provides an external perspective on IT effectiveness and helps identify areas where the organization is lagging or excelling. Metrics for benchmarking can include:
- Operational Efficiency: IT spending as a percentage of revenue, help desk resolution times, system uptime, application performance.
- Cost-Effectiveness: Total cost of ownership (TCO) for IT assets, cost per user, cost per transaction.
- Security Posture: Number of security incidents, time to detect and respond to threats, compliance audit results.
- User Satisfaction: Surveys and feedback on IT services, application usability, and support.
Benchmarking data can be obtained from industry reports, consulting firms, or peer organizations. It helps set realistic targets for improvement and identifies areas for strategic investment.
Gap Analysis and SWOT Assessment
Once the infrastructure, systems, capabilities, and performance have been assessed, a gap analysis and SWOT (Strengths, Weaknesses, Opportunities, Threats) assessment can be conducted. This synthesizes the findings and provides a clear picture of the current state relative to desired outcomes.
- Gap Analysis: Identifies the discrepancies between the current IT state and the desired future state. This highlights areas where technology, processes, or skills need to be developed or improved to achieve strategic objectives. For example, a gap might be identified in cloud adoption if the future vision involves significant cloud migration, but current capabilities are limited.
- SWOT Assessment: This widely used strategic planning tool provides a structured framework for evaluating the internal and external factors affecting the IT organization [3].
- Strengths (Internal): Internal factors that give the IT organization an advantage. Examples include a highly skilled IT team, robust existing infrastructure, strong security protocols, or efficient IT processes.
- Weaknesses (Internal): Internal limitations that hinder IT performance or the achievement of strategic goals. Examples include outdated technology, skill gaps, inefficient processes, or lack of integration between systems.
- Opportunities (External): External factors that present potential for growth or competitive advantage for the IT organization. Examples include emerging technologies (e.g., AI, IoT), favorable market trends, or new vendor partnerships.
- Threats (External): External factors that could negatively impact the IT organization or the business. Examples include increasing cybersecurity threats, regulatory changes, economic downturns, or competitive pressures.
The SWOT analysis provides a holistic view, enabling the IT strategy to capitalize on strengths, address weaknesses, leverage opportunities, and mitigate threats.
Risk and Security Posture Review
An integral part of the current state assessment is a comprehensive review of the organization's IT risk and security posture. This involves identifying potential vulnerabilities, assessing the likelihood and impact of various risks, and evaluating existing security controls. Key aspects include:
- Cybersecurity Risk Assessment: Identify potential cyber threats (e.g., malware, phishing, ransomware), assess vulnerabilities in systems and networks, and evaluate the effectiveness of current security measures (e.g., firewalls, intrusion detection systems, encryption).
- Data Privacy and Compliance: Review adherence to relevant data privacy regulations (e.g., GDPR, CCPA) and industry-specific compliance standards. Assess data handling practices, access controls, and data retention policies.
- Business Continuity and Disaster Recovery (BCDR): Evaluate the plans and capabilities for maintaining critical business operations during and after disruptive events (e.g., natural disasters, system outages). Assess recovery time objectives (RTO) and recovery point objectives (RPO).
- Third-Party Risk Management: Assess the security posture and compliance of third-party vendors and service providers who have access to organizational data or systems.
The outcome of this review should be a clear understanding of the organization's risk exposure and the effectiveness of its current risk mitigation strategies. This information is crucial for developing a robust cybersecurity strategy and integrating risk management throughout the IT roadmap.
References
[1] Electric AI. (2023, April 6). What is an IT Strategy? Framework & Examples. Retrieved from https://www.electric.ai/blog/guide-to-it-strategy [2] CIO Wiki. (2023, August 11). IT Strategy Framework. Retrieved from https://cio-wiki.org/wiki/IT_Strategy_Framework [3] Quantive. Top 10 Strategic Planning Frameworks & How to Use Them. Retrieved from https://quantive.com/resources/articles/top-strategic-frameworks
🚀5. Future State Vision and Objectives
Defining a clear and compelling future state vision is paramount for any IT strategy. This vision articulates where the organization wants to be in terms of its technology capabilities and how IT will enable future business success. It serves as a guiding star, providing direction for all subsequent strategic initiatives and investments. The future state vision is not merely a technical aspiration but a strategic declaration of how technology will transform the organization.
Technology Vision Statement
A technology vision statement is a concise, inspiring declaration that describes the desired future state of IT within the organization. It should be aspirational yet achievable, and clearly communicate the role of technology in realizing the overall business vision. A well-crafted vision statement should:
- Be Forward-Looking: Focus on the future and how technology will evolve to meet emerging needs.
- Be Business-Centric: Emphasize the value IT brings to the business, rather than just technical capabilities.
- Be Inspiring: Motivate stakeholders and provide a clear sense of purpose for IT initiatives.
- Be Concise and Memorable: Easy to understand and recall by all employees.
Example Vision Statement: "To be a leading digital innovator, leveraging cutting-edge technology to deliver seamless customer experiences, drive operational excellence, and foster a data-driven culture that empowers every employee."
Strategic IT Objectives
Strategic IT objectives translate the high-level technology vision into specific, measurable goals. These objectives should be SMART (Specific, Measurable, Achievable, Relevant, Time-bound) and directly align with the organization's overall business objectives. They provide the framework for measuring progress and success. Typical strategic IT objectives might include:
- Enhance Customer Experience: Improve digital channels, personalize interactions, and streamline service delivery through technology.
- Drive Operational Efficiency: Automate processes, optimize workflows, and reduce manual effort through IT solutions.
- Strengthen Cybersecurity Posture: Implement advanced security measures, reduce vulnerabilities, and enhance incident response capabilities to protect organizational assets.
- Foster Data-Driven Decision Making: Establish robust data governance, analytics platforms, and business intelligence tools to enable informed decision-making across all levels.
- Modernize IT Infrastructure: Migrate to cloud-native architectures, adopt scalable platforms, and enhance network capabilities to support future growth and agility.
- Cultivate a Culture of Innovation: Establish mechanisms for exploring and adopting emerging technologies, fostering experimentation, and encouraging technological literacy across the organization.
- Optimize IT Cost Efficiency: Implement cost-effective solutions, rationalize IT spending, and demonstrate clear ROI for technology investments.
Each objective should have associated key performance indicators (KPIs) and targets to track progress and evaluate achievement.
Target Operating Model
The Target Operating Model (TOM) describes the desired future state of how the IT function will operate to deliver the strategic IT objectives. It encompasses the organizational structure, processes, people, and technology required to achieve the vision. A well-defined TOM ensures that the IT organization is designed to effectively support the business strategy. Key components of a TOM include:
- Organizational Structure: The future organizational design of the IT department, including roles, responsibilities, reporting lines, and potential for centralized, decentralized, or hybrid models.
- Processes: Optimized and standardized IT processes (e.g., IT Service Management, Project Management, Application Development, Infrastructure Operations) that support efficiency and effectiveness.
- People and Capabilities: The required skills, competencies, and talent management strategies to support the future state. This includes training, recruitment, and retention plans.
- Technology and Applications: The future state of the technology stack, including core systems, platforms, and applications that will enable the strategic objectives.
- Governance and Sourcing: The mechanisms for decision-making, oversight, and how IT services will be delivered (e.g., in-house, outsourced, co-sourced).
Developing a TOM helps identify the changes required in the current operating model and provides a roadmap for transformation.
Success Metrics and KPIs
To effectively measure the achievement of the future state vision and strategic IT objectives, a comprehensive set of success metrics and Key Performance Indicators (KPIs) must be defined. These metrics provide tangible evidence of progress and allow for continuous monitoring and adjustment of the IT strategy. KPIs should be aligned with both IT and business outcomes. Examples include:
- Business Outcome KPIs: Revenue growth attributed to digital initiatives, customer satisfaction scores (CSAT), operational cost reduction, market share increase.
- IT Service Delivery KPIs: System uptime, incident resolution time, service request fulfillment rate, application performance.
- Innovation KPIs: Number of new digital products/services launched, adoption rate of new technologies, percentage of budget allocated to innovation.
- Security KPIs: Number of security incidents, time to detect and contain threats, compliance audit scores.
- Financial KPIs: IT spend as a percentage of revenue, ROI of IT projects, cost per user.
- Employee Engagement KPIs: IT staff retention rate, employee satisfaction with IT services, training completion rates.
Regular reporting and analysis of these KPIs are essential for demonstrating the value of IT and ensuring accountability.
Alignment with Business Goals
The future state vision and objectives must be inextricably linked to the overall business goals. This alignment ensures that IT is not merely a support function but a strategic partner in achieving organizational success. Mechanisms to ensure this alignment include:
- Joint Strategic Planning Sessions: Regular workshops and planning sessions involving both IT and business leadership to co-create the vision and objectives.
- Business Relationship Management (BRM): Dedicated roles or functions within IT that serve as liaisons to business units, understanding their needs and ensuring IT solutions meet those requirements.
- Shared Governance Structures: Establishing steering committees or working groups with representation from both IT and business to oversee strategic initiatives and make joint decisions.
- Value Realization Frameworks: Implementing methodologies to track and report the business value generated by IT investments, demonstrating the tangible impact on organizational goals.
By embedding IT within the core business strategy, organizations can ensure that technology investments are purposeful, impactful, and contribute directly to competitive advantage.
🔮6. Technology Trends and Emerging Technologies
🤖Transformative Technology Landscape 2025
In an era of rapid technological evolution, an effective IT strategy must proactively identify, evaluate, and integrate relevant technology trends and emerging innovations. This isn't merely about adopting new tools—it's about strategically positioning the organization for future success.
Strategic Focus: Leveraging trends to drive competitive advantage, enhance operational efficiency, and foster continuous innovation in the dynamic technology landscape.
Current Technology Trends Analysis
The current technology landscape is shaped by several transformative trends that are redefining business operations and customer interactions. Understanding these trends is crucial for developing an IT strategy that remains relevant and impactful. Key trends influencing IT strategies in 2025 and beyond include:
🎯Key Technology Trends 2025:
- Artificial Intelligence (AI) and Machine Learning (ML): AI continues to be a foundational amplifier across various domains. It is evolving beyond mere automation to enable advanced analytics, predictive capabilities, and intelligent decision-making. This includes the rapid growth of Generative AI, which creates new content, and Applied AI, which focuses on practical applications across industries [4]. Organizations are leveraging AI for enhanced customer service (e.g., chatbots), optimized operations (e.g., predictive maintenance), and deeper insights from vast datasets.
- Agentic AI: A rapidly emerging focus, Agentic AI combines the flexibility of AI foundation models with the ability to act autonomously. These 'virtual coworkers' can plan and execute multi-step workflows, signaling potentially revolutionary possibilities for enterprise and consumer technology [4]. This trend points towards more sophisticated automation and intelligent assistance.
- Application-Specific Semiconductors: The demand for specialized hardware to support compute-intensive workloads, particularly from AI training and inference, is driving innovation in semiconductors. These advancements are crucial for managing cost, heat, and power consumption, enabling the continued scaling of AI and other advanced technologies [4].
- The Rise of Autonomous Systems: Autonomous systems, encompassing physical robots and digital agents, are transitioning from pilot projects to practical applications. These systems are not just executing tasks but are learning, adapting, and collaborating, moving towards broad deployment in areas like logistics, dynamic environment navigation, and virtual assistance [4].
- New Human-Machine Collaboration Models: The interaction between humans and machines is entering a new phase characterized by more natural interfaces, multimodal inputs, and adaptive intelligence. This evolution emphasizes augmentation rather than replacement, fostering more productive collaboration between people and intelligent systems through tools like voice-driven copilots and sensor-enabled wearables [4].
- Cloud Computing Evolution: Beyond basic infrastructure, cloud strategies are maturing to focus on hybrid and multi-cloud environments, edge computing, and serverless architectures. The emphasis is on optimizing cloud spend, enhancing security in cloud environments, and leveraging cloud-native services for agility and scalability.
- Cybersecurity Mesh Architecture: As organizations expand their digital footprint, a distributed and composable security approach is gaining traction. This architecture enables a more adaptive and resilient security posture, integrating disparate security services into a cohesive framework.
- Data Fabric: This architecture provides a consistent and unified view of data across disparate sources, enabling seamless data access, integration, and governance. It is critical for supporting advanced analytics, AI initiatives, and real-time decision-making.
- Sustainable Technology: Growing environmental concerns are driving the adoption of sustainable IT practices, including energy-efficient hardware, green data centers, and optimizing IT operations to reduce carbon footprint. This trend aligns IT strategy with corporate social responsibility goals.
Emerging Technology Evaluation
Beyond current trends, organizations must establish a systematic approach to evaluate emerging technologies that could disrupt existing business models or create new opportunities. This involves:
- Technology Scouting: Continuously monitoring the technology landscape for nascent innovations, research breakthroughs, and startup activities that could have future relevance.
- Proof of Concept (POC) and Pilot Programs: Experimenting with promising emerging technologies through small-scale POCs and pilot programs to assess their feasibility, potential impact, and integration challenges before large-scale investment.
- Risk-Benefit Analysis: Conducting thorough analyses to understand the potential benefits (e.g., competitive advantage, cost savings, new revenue streams) against the risks (e.g., technical maturity, security vulnerabilities, integration complexity, talent requirements) associated with adopting new technologies.
- Vendor Ecosystem Assessment: Evaluating the maturity and reliability of vendors offering emerging technology solutions, considering their support, roadmap, and partnership models.
Technology Adoption Roadmap
Once emerging technologies are evaluated and deemed strategically valuable, a clear adoption roadmap is essential. This roadmap outlines the phased approach for integrating new technologies into the organization. Key considerations include:
- Phased Rollout: Implementing new technologies in stages, starting with pilot groups or specific business units, to minimize disruption and gather feedback for refinement.
- Integration Strategy: Planning for seamless integration with existing systems and processes to avoid data silos and operational inefficiencies.
- Skill Development: Identifying the new skills required to manage and leverage the adopted technologies and developing training programs or recruitment strategies to address skill gaps.
- Change Management: Proactively managing the organizational and cultural changes associated with new technology adoption, ensuring user acceptance and maximizing benefits.
- Scalability Planning: Designing solutions that can scale to meet future demands and accommodate organizational growth.
Innovation Strategy and R&D Priorities
An IT strategy should also encompass a clear innovation strategy and define research and development (R&D) priorities. This fosters a culture of continuous improvement and ensures the organization remains at the forefront of technological advancements. Key elements include:
- Dedicated Innovation Labs or Teams: Establishing internal units focused on exploring, experimenting with, and developing innovative technology solutions.
- Partnerships and Ecosystem Engagement: Collaborating with external partners, startups, academic institutions, and industry consortia to co-create solutions and gain access to cutting-edge research.
- Open Innovation: Encouraging ideas and contributions from employees across all departments, fostering a culture where innovation is everyone's responsibility.
- Funding for Innovation: Allocating dedicated budgets for R&D, experimentation, and proof-of-concept initiatives.
- Intellectual Property Management: Developing strategies for protecting and leveraging intellectual property generated through innovation efforts.
By systematically addressing technology trends and fostering a proactive innovation culture, organizations can ensure their IT strategy is not just reactive to change but a driving force for future success.
References
[1] Electric AI. (2023, April 6). What is an IT Strategy? Framework & Examples. Retrieved from https://www.electric.ai/blog/guide-to-it-strategy [2] CIO Wiki. (2023, August 11). IT Strategy Framework. Retrieved from https://cio-wiki.org/wiki/IT_Strategy_Framework [3] Quantive. Top 10 Strategic Planning Frameworks & How to Use Them. Retrieved from https://quantive.com/resources/articles/top-strategic-frameworks [4] McKinsey. (2025, July 22). McKinsey technology trends outlook 2025. Retrieved from https://www.mckinsey.com/capabilities/mckinsey-digital/our-insights/the-top-trends-in-tech
⚡7. Strategic Initiatives and Programs
Translating the IT strategy into actionable plans requires the identification, definition, and management of strategic initiatives and programs. This section outlines the process for prioritizing these initiatives, allocating resources, and planning their execution to ensure they deliver tangible value and contribute to the overall strategic objectives.
Priority IT Initiatives Identification
Strategic IT initiatives are the key projects and programs that will bridge the gap between the current state and the desired future state. Their identification should be a collaborative process involving IT and business leadership, leveraging the insights gained from the current state assessment and future state visioning. Key considerations for identifying priority initiatives include:
- Alignment with Strategic Objectives: Each initiative must directly contribute to one or more defined strategic IT objectives and, by extension, to the overall business goals.
- Impact and Value: Assess the potential impact of each initiative on business outcomes, such as revenue growth, cost reduction, efficiency gains, risk mitigation, or customer satisfaction.
- Feasibility and Risk: Evaluate the technical feasibility, resource availability, organizational readiness, and potential risks associated with each initiative. Consider factors like complexity, interdependencies, and external dependencies.
- Cost-Benefit Analysis: Conduct a preliminary cost-benefit analysis to understand the potential return on investment (ROI) and justify the allocation of resources.
- Urgency and Time Sensitivity: Prioritize initiatives that address critical pain points, regulatory requirements, or time-sensitive market opportunities.
Techniques such as weighted scoring models, portfolio matrices (e.g., BCG Matrix, Ansoff Matrix adapted for IT initiatives), and stakeholder workshops can be used to facilitate the identification and initial prioritization of these initiatives.
Program Portfolio Management
Once strategic initiatives are identified, they are typically grouped into programs and managed as a portfolio to ensure coordinated execution and optimal resource utilization. Program portfolio management involves:
- Program Definition: Grouping related projects and initiatives under a common program umbrella to achieve a larger strategic objective. For example, a "Digital Transformation Program" might encompass projects related to cloud migration, AI implementation, and data analytics platform development.
- Resource Allocation: Strategically allocating financial, human, and technological resources across the entire portfolio to maximize value and ensure that critical initiatives are adequately funded and staffed.
- Dependency Management: Identifying and managing interdependencies between projects and programs within the portfolio to prevent bottlenecks and ensure smooth execution.
- Risk Aggregation and Management: Assessing and managing risks at the portfolio level, considering how individual project risks might impact the overall strategic objectives.
- Performance Monitoring: Continuously monitoring the progress and performance of the entire portfolio against strategic goals and KPIs, making adjustments as needed.
Effective program portfolio management ensures that the organization is investing in the right initiatives and that these initiatives are delivering the expected strategic benefits.
Resource Allocation and Budgeting
Accurate resource allocation and budgeting are crucial for the successful execution of strategic IT initiatives. This involves:
- Detailed Cost Estimation: Developing comprehensive cost estimates for each initiative, including capital expenditures (CapEx) for hardware and software, and operational expenditures (OpEx) for ongoing maintenance, support, and cloud services.
- Resource Planning: Identifying the human resources (internal staff, contractors, consultants) and technological resources (licenses, infrastructure) required for each initiative, considering both current availability and future needs.
- Budget Approval Process: Establishing a clear process for budget submission, review, and approval, ensuring alignment with financial governance policies.
- Financial Tracking and Control: Implementing robust mechanisms for tracking actual expenditures against budgeted amounts, identifying variances, and taking corrective actions.
- Funding Models: Exploring various funding models, such as project-based funding, value-based funding, or chargeback models, to ensure sustainable investment in IT.
Timeline and Milestone Planning
A well-defined timeline with clear milestones is essential for managing expectations, tracking progress, and ensuring accountability. This involves:
- Phased Approach: Breaking down large initiatives into smaller, manageable phases with defined deliverables and completion criteria.
- Milestone Definition: Establishing key milestones that represent significant achievements or decision points within each initiative. These milestones serve as checkpoints for progress review.
- Dependency Mapping: Identifying and mapping dependencies between tasks and initiatives to create a realistic and achievable timeline.
- Gantt Charts and Roadmaps: Utilizing project management tools (e.g., Gantt charts, visual roadmaps) to visualize timelines, dependencies, and resource allocation.
- Regular Progress Reviews: Conducting regular reviews with stakeholders to assess progress against milestones, identify potential delays, and make necessary adjustments.
Dependencies and Risk Management
Strategic initiatives often have complex interdependencies and inherent risks that must be proactively managed. This involves:
- Interdependency Mapping: Identifying and documenting dependencies between different initiatives, projects, and external factors. This helps in understanding potential ripple effects and planning for coordinated execution.
- Risk Identification and Assessment: Continuously identifying potential risks (e.g., technical challenges, resource constraints, vendor issues, security threats, regulatory changes) that could impact the successful delivery of initiatives. Assess the likelihood and impact of each risk.
- Risk Mitigation Strategies: Developing and implementing strategies to mitigate identified risks. This could include contingency plans, alternative approaches, or additional resource allocation.
- Risk Monitoring and Reporting: Regularly monitoring the status of identified risks, tracking the effectiveness of mitigation strategies, and reporting on risk exposure to relevant stakeholders.
- Contingency Planning: Developing backup plans for critical initiatives in case primary plans encounter significant obstacles.
By systematically managing dependencies and risks, organizations can increase the likelihood of successful IT strategy execution and minimize disruptions.
🛠️8. Implementation Methodology
Successful execution of an IT strategy hinges on a well-defined and robust implementation methodology. This section outlines the approach to translating strategic plans into tangible outcomes, emphasizing structured processes, effective change management, and rigorous quality assurance. A comprehensive methodology ensures that initiatives are delivered efficiently, meet their objectives, and are adopted effectively across the organization.
Phased Implementation Approach
Large-scale IT strategic initiatives are best managed through a phased implementation approach. This breaks down complex transformations into smaller, manageable stages, allowing for iterative development, continuous feedback, and reduced risk. A typical phased approach includes:
- Phase 1: Planning and Design: In-depth planning, detailed requirements gathering, architectural design, and selection of technologies and vendors. This phase culminates in a comprehensive project plan and design specifications.
- Phase 2: Development and Configuration: Building, configuring, and customizing systems and applications according to the design specifications. This may involve coding, integration, and data migration activities.
- Phase 3: Testing and Quality Assurance: Rigorous testing of all components, including unit testing, integration testing, system testing, user acceptance testing (UAT), and performance testing, to ensure functionality, reliability, and security.
- Phase 4: Deployment and Go-Live: The controlled release of the new systems or capabilities into the production environment. This includes data migration, system cutover, and initial user support.
- Phase 5: Post-Implementation Review and Optimization: Monitoring system performance, gathering user feedback, addressing post-launch issues, and identifying opportunities for continuous improvement and optimization.
This iterative approach allows for flexibility, enables early realization of benefits, and provides opportunities to learn and adapt throughout the implementation lifecycle.
Change Management Strategy
Technology implementations often fail not due to technical issues, but due to inadequate attention to the human element. A comprehensive change management strategy is essential to ensure user adoption, minimize resistance, and maximize the benefits of new IT initiatives. Key components include:
- Stakeholder Analysis: Identifying all individuals and groups affected by the change, understanding their concerns, and assessing their readiness for change.
- Communication Plan: Developing a clear and consistent communication strategy to inform stakeholders about the changes, their benefits, timelines, and how they will be impacted. This includes regular updates and feedback channels.
- Training and Skill Development: Providing adequate training programs and resources to equip users with the necessary skills to effectively utilize new systems and processes.
- Resistance Management: Proactively identifying potential sources of resistance and developing strategies to address them through engagement, education, and support.
- Sponsorship and Leadership Buy-in: Ensuring strong and visible sponsorship from executive leadership to champion the change and reinforce its importance.
- Reinforcement Mechanisms: Establishing mechanisms to reinforce the change, such as performance incentives, recognition programs, and ongoing support structures.
Effective change management transforms potential obstacles into opportunities for successful adoption and sustained value creation.
Project Management Framework
A consistent and disciplined project management framework is vital for controlling scope, schedule, budget, and quality across all IT initiatives. While specific methodologies may vary (e.g., Agile, Waterfall, Hybrid), a robust framework typically includes:
- Project Governance: Defining roles, responsibilities, decision-making authority, and reporting structures for each project.
- Scope Management: Clearly defining project boundaries, deliverables, and acceptance criteria to prevent scope creep.
- Schedule Management: Developing realistic project timelines, identifying critical paths, and tracking progress against milestones.
- Cost Management: Estimating, budgeting, and controlling project costs to ensure adherence to financial targets.
- Quality Management: Establishing quality standards, conducting reviews and inspections, and implementing testing procedures to ensure deliverables meet requirements.
- Risk Management: Continuously identifying, assessing, and mitigating project-level risks.
- Communication Management: Establishing clear communication channels and reporting mechanisms to keep stakeholders informed.
- Stakeholder Management: Engaging and managing the expectations of all project stakeholders.
Utilizing a standardized project management methodology (e.g., PMBOK, PRINCE2) and appropriate tools (e.g., Jira, Microsoft Project) enhances predictability and success rates.
Quality Assurance and Testing
Ensuring the quality and reliability of IT solutions is paramount. A comprehensive quality assurance (QA) and testing strategy is integrated throughout the development lifecycle to identify and rectify defects early. Key aspects include:
- Test Planning: Developing detailed test plans that outline testing objectives, scope, types of testing, test environments, and entry/exit criteria.
- Test Types: Conducting various types of testing, including:
- Unit Testing: Testing individual components or modules.
- Integration Testing: Verifying the interactions between different modules or systems.
- System Testing: Testing the complete integrated system against functional and non-functional requirements.
- User Acceptance Testing (UAT): Business users validate the system against their requirements in a realistic environment.
- Performance Testing: Assessing system responsiveness, stability, and scalability under various load conditions.
- Security Testing: Identifying vulnerabilities and weaknesses in the system.
- Regression Testing: Ensuring that new changes do not adversely affect existing functionality.
- Defect Management: Establishing a systematic process for logging, tracking, prioritizing, and resolving defects.
- Automation Testing: Leveraging automation tools to increase testing efficiency and coverage, particularly for regression testing.
Rigorous QA and testing minimize post-implementation issues, enhance user satisfaction, and protect organizational reputation.
Communication and Training Plans
Effective communication and comprehensive training are critical enablers for successful IT strategy implementation. These plans ensure that all stakeholders are informed, engaged, and equipped to adapt to new technologies and processes.
- Communication Plan: Defines the what, who, when, and how of communication throughout the implementation lifecycle. It includes:
- Key Messages: Consistent messaging about the strategy, its benefits, and progress.
- Target Audiences: Tailoring communications to different stakeholder groups (e.g., executives, managers, end-users).
- Channels: Utilizing appropriate communication channels (e.g., emails, newsletters, town halls, dedicated portals, workshops).
- Frequency: Establishing a regular cadence for updates and feedback sessions.
- Feedback Mechanisms: Providing avenues for stakeholders to ask questions, raise concerns, and provide input.
- Training Plan: Outlines the strategy for educating users on new systems, applications, and processes. It includes:
- Training Needs Analysis: Identifying specific training requirements for different user groups based on their roles and responsibilities.
- Training Modalities: Selecting appropriate training methods (e.g., in-person workshops, online courses, webinars, self-paced modules, job aids).
- Curriculum Development: Designing and developing training materials that are relevant, practical, and engaging.
- Training Delivery: Scheduling and delivering training sessions, ensuring accessibility and flexibility.
- Post-Training Support: Providing ongoing support through help desks, FAQs, and super-user networks to reinforce learning and address issues.
Well-executed communication and training plans foster a sense of ownership, build confidence, and drive successful adoption of the new IT landscape.
🏛️9. Governance and Organization
Effective IT governance and a well-structured IT organization are fundamental to the successful implementation and sustained value realization of any IT strategy. This section details the mechanisms for decision-making, accountability, and oversight within the IT domain, ensuring alignment with business objectives and efficient resource utilization.
IT Governance Structure
IT governance defines the framework of leadership, organizational structures, and processes that ensure the organization’s IT sustains and extends the organization’s strategies and objectives. A robust IT governance structure typically includes:
- IT Steering Committee: A high-level committee comprising executive business leaders and IT leadership. Its primary role is to provide strategic direction, approve major IT investments, prioritize initiatives, and monitor overall IT performance and alignment with business goals.
- IT Architecture Review Board (ARB): Responsible for reviewing and approving IT architecture standards, designs, and solutions to ensure consistency, scalability, security, and alignment with the enterprise architecture vision.
- Project/Program Governance Boards: Dedicated boards or committees for major IT projects or programs, responsible for overseeing project progress, managing risks, resolving issues, and ensuring adherence to scope, budget, and schedule.
- Data Governance Council: A cross-functional body focused on establishing and enforcing policies, standards, and processes for data quality, security, privacy, and usability across the organization.
- Security Governance Committee: Oversees the organization’s cybersecurity posture, reviews security policies, assesses risks, and ensures compliance with security regulations and best practices.
These structures ensure that IT decisions are made transparently, with appropriate input from all stakeholders, and are aligned with the organization’s strategic direction.
Roles and Responsibilities
Clearly defined roles and responsibilities within the IT organization and across business functions are essential for accountability and efficient operations. This includes:
- Chief Information Officer (CIO) / Chief Technology Officer (CTO): Strategic leadership for IT, aligning IT with business strategy, driving innovation, and overseeing IT operations.
- IT Department Heads (e.g., Infrastructure, Applications, Security, Data): Responsible for the operational management and delivery within their respective domains, ensuring technical excellence and service delivery.
- Business Relationship Managers (BRMs): Act as liaisons between IT and specific business units, understanding business needs, communicating IT capabilities, and ensuring IT solutions meet business requirements.
- Enterprise Architects: Responsible for defining the overall IT architecture, standards, and roadmaps, ensuring coherence and integration across systems.
- Project Managers / Program Managers: Lead the planning, execution, and delivery of IT projects and programs, managing scope, budget, schedule, and resources.
- Data Stewards / Data Owners: Business users responsible for the quality, integrity, and appropriate use of specific data sets.
Defining these roles and their interdependencies minimizes confusion, improves collaboration, and enhances overall IT effectiveness.
Decision-Making Processes
Formalized decision-making processes ensure that IT-related choices are made efficiently, consistently, and with due consideration of all relevant factors. Key processes include:
- Strategic Decision-Making: Typically handled by the IT Steering Committee, focusing on major investments, strategic priorities, and policy formulation.
- Tactical Decision-Making: Made by IT leadership and governance boards, concerning project prioritization, resource allocation within programs, and architectural standards.
- Operational Decision-Making: Daily decisions related to IT operations, incident management, and service delivery, often made by IT managers and teams.
- Investment Approval Process: A structured process for evaluating, proposing, and approving IT investments, including business case development, financial analysis, and risk assessment.
- Change Control Process: A formal process for managing changes to IT systems, applications, and infrastructure, ensuring proper review, testing, and approval before implementation.
Steering Committee and Oversight
The IT Steering Committee plays a pivotal role in IT governance. Its functions include:
- Strategic Alignment: Ensuring that IT strategy and initiatives remain aligned with the overall business strategy and objectives.
- Investment Prioritization: Reviewing and approving major IT investments and prioritizing projects based on strategic value, ROI, and risk.
- Performance Monitoring: Reviewing IT performance against defined KPIs, service level agreements (SLAs), and budget adherence.
- Risk Management Oversight: Providing oversight of IT risks, including cybersecurity, data privacy, and operational risks, and ensuring appropriate mitigation strategies are in place.
- Policy and Standard Setting: Approving key IT policies, standards, and architectural guidelines.
- Issue Resolution: Providing a forum for resolving high-level IT-related issues and conflicts that cannot be resolved at lower levels.
Regular meetings (e.g., quarterly) with clear agendas, documented decisions, and actionable outcomes are essential for the effectiveness of the Steering Committee.
Vendor and Partner Management
As organizations increasingly rely on external vendors and partners for IT services, software, and infrastructure, effective management of these relationships becomes critical. This involves:
- Vendor Selection and Evaluation: A structured process for selecting vendors based on technical capabilities, financial stability, security posture, service level agreements (SLAs), and cultural fit.
- Contract Management: Meticulous management of contracts, ensuring that terms and conditions, service levels, and pricing are clearly defined and adhered to.
- Performance Monitoring: Regularly monitoring vendor performance against agreed-upon SLAs and KPIs, conducting service reviews, and providing feedback.
- Relationship Management: Building strong, collaborative relationships with key vendors and partners to foster mutual trust and facilitate problem-solving.
- Risk Management: Assessing and mitigating risks associated with third-party dependencies, including data security, business continuity, and compliance risks.
- Exit Strategy: Developing clear exit strategies for critical vendor relationships to ensure business continuity and minimize disruption in case of contract termination or change.
Effective vendor and partner management ensures that external dependencies contribute positively to the IT strategy and overall business objectives.
🔒10. Risk Management and Security
In today’s interconnected digital landscape, IT risk management and cybersecurity are not merely technical considerations but strategic imperatives. A comprehensive IT strategy roadmap must integrate robust frameworks for identifying, assessing, mitigating, and monitoring risks to protect organizational assets, ensure business continuity, and maintain trust. This section outlines the critical components of a proactive risk management and security strategy.
IT Risk Assessment Framework
An IT risk assessment framework provides a structured approach to systematically identify, analyze, and evaluate potential threats and vulnerabilities to an organization’s information systems and data. The goal is to understand the likelihood of a risk occurring and its potential impact, enabling informed decision-making on risk treatment. Key steps in a typical framework include:
- Asset Identification: Cataloging all critical IT assets, including hardware, software, data, networks, and intellectual property. Prioritize assets based on their value to the business.
- Threat Identification: Identifying potential threats that could exploit vulnerabilities, such as cyberattacks (malware, phishing, ransomware), natural disasters, human error, insider threats, and system failures.
- Vulnerability Identification: Discovering weaknesses in systems, applications, processes, or configurations that could be exploited by threats. This includes technical vulnerabilities, process weaknesses, and human factors.
- Risk Analysis: Assessing the likelihood of each threat exploiting a vulnerability and the potential impact (financial, reputational, operational, legal) if it occurs. This can be qualitative (high, medium, low) or quantitative (monetary value).
- Risk Evaluation: Comparing the analyzed risk levels against predefined risk criteria to determine the significance of the risk and prioritize them for treatment.
- Risk Treatment (Mitigation): Developing and implementing strategies to reduce, transfer, avoid, or accept risks. This often involves implementing security controls, updating policies, or investing in new technologies.
- Risk Monitoring and Review: Continuously monitoring the effectiveness of implemented controls, reassessing risks periodically, and adapting the framework to evolving threats and business changes.
Common frameworks like NIST Cybersecurity Framework, ISO 27005, and COBIT provide structured guidance for conducting IT risk assessments.
Cybersecurity Strategy
A robust cybersecurity strategy is paramount to protecting an organization’s digital assets from an ever-evolving threat landscape. It extends beyond technical controls to encompass people, processes, and technology. A comprehensive cybersecurity strategy should include:
- Defense-in-Depth: Implementing multiple layers of security controls (e.g., firewalls, intrusion detection/prevention systems, antivirus, encryption, multi-factor authentication) to create a resilient defense.
- Identity and Access Management (IAM): Establishing strong controls over user identities and their access privileges to systems and data, adhering to the principle of least privilege.
- Data Security: Protecting sensitive data throughout its lifecycle (at rest, in transit, in use) through encryption, data loss prevention (DLP) solutions, and strict access controls.
- Network Security: Securing network infrastructure through segmentation, intrusion detection, and secure configurations to prevent unauthorized access and data exfiltration.
- Endpoint Security: Protecting end-user devices (laptops, desktops, mobile devices) from malware and other threats through endpoint detection and response (EDR) solutions and regular patching.
- Application Security: Integrating security into the software development lifecycle (SDLC) to identify and remediate vulnerabilities in applications from design to deployment.
- Security Operations Center (SOC): Establishing capabilities for continuous monitoring, threat detection, incident response, and security event management.
- Threat Intelligence: Leveraging external threat intelligence feeds to stay informed about emerging threats and vulnerabilities, enabling proactive defense.
- Security Awareness Training: Regularly training employees on cybersecurity best practices, phishing awareness, and organizational security policies to reduce human-related risks.
Business Continuity and Disaster Recovery
Business Continuity Planning (BCP) and Disaster Recovery (DRP) are critical components of an IT strategy, ensuring that an organization can continue essential operations and recover from disruptive events. These plans focus on minimizing downtime and data loss.
- Business Impact Analysis (BIA): Identifying critical business processes and systems, and assessing the impact of their disruption. This determines Recovery Time Objectives (RTOs) – the maximum tolerable downtime, and Recovery Point Objectives (RPOs) – the maximum tolerable data loss.
- Disaster Recovery Planning (DRP): Developing detailed plans for restoring IT systems and data after a disaster. This includes backup and recovery procedures, offsite storage, redundant infrastructure, and failover mechanisms.
- Business Continuity Planning (BCP): Broader than DRP, BCP focuses on maintaining essential business functions during and after a disruption. It includes strategies for alternative work locations, communication plans, and critical vendor management.
- Regular Testing and Drills: Periodically testing BCP/DRP plans through simulations and drills to identify gaps, validate recovery procedures, and ensure personnel are familiar with their roles.
- Documentation and Maintenance: Maintaining up-to-date documentation of all BCP/DRP plans, procedures, and contact information, and reviewing them regularly to reflect changes in IT infrastructure or business processes.
Compliance and Regulatory Requirements
Adherence to relevant compliance and regulatory requirements is a non-negotiable aspect of IT strategy. Failure to comply can result in significant fines, legal penalties, and reputational damage. The IT strategy must incorporate mechanisms to ensure ongoing compliance with:
- Industry-Specific Regulations: (e.g., HIPAA for healthcare, PCI DSS for payment card industry, SOX for financial reporting).
- Data Privacy Regulations: (e.g., GDPR, CCPA, LGPD) governing the collection, processing, storage, and sharing of personal data.
- Government Regulations: (e.g., national cybersecurity laws, data localization requirements).
- Internal Policies: Adherence to the organization’s own IT security, data handling, and acceptable use policies.
This involves implementing controls, conducting regular audits, maintaining detailed records, and staying informed about changes in the regulatory landscape.
Risk Mitigation Strategies
Once risks are identified and assessed, appropriate mitigation strategies must be developed and implemented. These strategies aim to reduce the likelihood or impact of risks to an acceptable level. Common approaches include:
- Risk Avoidance: Eliminating the activity or technology that gives rise to the risk.
- Risk Reduction: Implementing controls to decrease the likelihood or impact of a risk (e.g., stronger security controls, redundant systems, employee training).
- Risk Transfer: Shifting the financial impact of a risk to a third party, typically through insurance or outsourcing.
- Risk Acceptance: Acknowledging the risk and deciding to take no action, usually because the cost of mitigation outweighs the potential impact, or the likelihood is very low. This must be a conscious, documented decision.
Effective risk mitigation requires a continuous cycle of assessment, planning, implementation, and monitoring, integrated into the daily operations and strategic planning of the IT function.
📈11. Performance Management and Measurement
Effective performance management and measurement are crucial for ensuring that the IT strategy delivers its intended value and remains aligned with business objectives. This section outlines the frameworks and processes for monitoring, evaluating, and reporting on the performance of IT initiatives and the overall IT function. Continuous measurement enables data-driven decision-making, fosters accountability, and drives continuous improvement.
KPI Framework and Metrics
A robust Key Performance Indicator (KPI) framework is essential for translating strategic IT objectives into measurable outcomes. KPIs should be carefully selected to provide insights into both the efficiency of IT operations and the effectiveness of IT in supporting business goals. The framework should include a balanced set of metrics across various dimensions:
- Financial Metrics:
- IT Spend as % of Revenue/Operating Expense: Measures the proportion of organizational resources allocated to IT.
- Return on Investment (ROI) of IT Projects: Quantifies the financial benefits generated by IT investments relative to their costs.
- Total Cost of Ownership (TCO): Comprehensive cost analysis of IT assets over their lifecycle.
- Cost per User/Service: Efficiency metric for IT service delivery.
- Operational Metrics:
- System Uptime/Availability: Percentage of time IT systems are operational and accessible.
- Incident Resolution Time (Mean Time To Resolve - MTTR): Average time taken to resolve IT incidents.
- Change Success Rate: Percentage of IT changes implemented without issues.
- Service Request Fulfillment Rate: Percentage of service requests completed within agreed-upon service levels.
- Network Latency/Bandwidth Utilization: Performance indicators for network infrastructure.
- Customer/User Satisfaction Metrics:
- IT Service Satisfaction Scores: Feedback from users on the quality of IT services and support.
- Application Usability Scores: User ratings on the ease of use and effectiveness of IT applications.
- Net Promoter Score (NPS) for IT: Measures user loyalty and willingness to recommend IT services.
- Innovation and Growth Metrics:
- Number of New Digital Products/Services Launched: Quantifies the output of innovation efforts.
- Adoption Rate of New Technologies: Measures how quickly and widely new IT solutions are embraced by users.
- Time to Market for New Features: Speed at which new functionalities are delivered.
- Security and Compliance Metrics:
- Number of Security Incidents/Breaches: Tracks the occurrence of security events.
- Vulnerability Patching Cadence: Measures the timeliness of applying security patches.
- Compliance Audit Scores: Results from internal and external compliance assessments.
- Mean Time To Detect (MTTD) / Mean Time To Contain (MTTC) Threats: Speed of identifying and mitigating security threats.
Each KPI should have a clear definition, a target value, and a responsible owner.
Performance Monitoring Systems
To effectively track and report on KPIs, organizations need robust performance monitoring systems. These systems collect, aggregate, and visualize data from various IT sources, providing real-time insights into performance. Key components include:
- IT Service Management (ITSM) Tools: For tracking incidents, service requests, changes, and problem management.
- Network Performance Monitoring (NPM) Tools: For real-time monitoring of network health, traffic, and latency.
- Application Performance Monitoring (APM) Tools: For monitoring the performance and availability of software applications.
- Security Information and Event Management (SIEM) Systems: For collecting and analyzing security logs and events to detect threats.
- Business Intelligence (BI) and Data Visualization Tools: For creating dashboards and reports that present IT performance data in an easily digestible format for various stakeholders.
- Cloud Cost Management Platforms: For monitoring and optimizing cloud spending across different services.
These systems provide the necessary data infrastructure for continuous performance measurement and enable proactive identification of issues.
Regular Review and Assessment Processes
Performance measurement is not a one-time activity but an ongoing process of regular review and assessment. This ensures that the IT strategy remains on track, adapts to changing circumstances, and delivers continuous value. Key processes include:
- Daily/Weekly Operational Reviews: Short, frequent meetings within IT teams to review operational metrics, address immediate issues, and track progress on short-term goals.
- Monthly Performance Reviews: More detailed reviews with IT leadership to assess departmental performance against KPIs, discuss trends, and identify areas for improvement.
- Quarterly Strategic Reviews: Meetings with the IT Steering Committee and key business stakeholders to review progress against strategic IT objectives, assess the overall health of the IT strategy, and make necessary adjustments to priorities or resource allocation.
- Annual IT Strategy Review: A comprehensive annual assessment of the entire IT strategy, including a re-evaluation of the current state, future vision, and alignment with evolving business goals. This review informs the planning cycle for the next year.
- Post-Implementation Reviews (PIRs): Formal reviews conducted after the completion of major IT projects to assess their success against initial objectives, identify lessons learned, and capture best practices for future initiatives.
These reviews foster accountability, facilitate communication, and ensure that performance insights lead to actionable improvements.
Continuous Improvement Methodology
An effective IT strategy embraces a culture of continuous improvement, recognizing that optimization is an ongoing journey rather than a destination. Methodologies such as Lean, Six Sigma, Agile, and DevOps can be applied to IT processes to drive efficiency and effectiveness. Key elements include:
- Feedback Loops: Establishing formal and informal mechanisms for collecting feedback from users, business stakeholders, and IT staff to identify pain points and areas for improvement.
- Root Cause Analysis: Systematically investigating the underlying causes of performance issues or failures to implement effective long-term solutions.
- Process Optimization: Regularly reviewing and refining IT processes to eliminate waste, reduce bottlenecks, and enhance efficiency.
- Automation: Leveraging automation technologies to streamline repetitive tasks, reduce manual errors, and free up IT staff for more strategic activities.
- Knowledge Management: Building and maintaining a centralized knowledge base to capture lessons learned, best practices, and solutions, facilitating knowledge sharing and reducing rework.
- Benchmarking and Best Practice Adoption: Continuously seeking out and adopting industry best practices and benchmarking against high-performing organizations to drive excellence.
Reporting and Dashboard Requirements
Clear, concise, and actionable reporting is essential for communicating IT performance to various stakeholders. Dashboards provide a visual summary of key metrics, enabling quick understanding and informed decision-making. Reporting and dashboard requirements should consider:
- Audience-Specific Reporting: Tailoring reports and dashboards to the needs and interests of different audiences (e.g., executive summary for leadership, detailed operational reports for IT managers, user-centric dashboards for business units).
- Key Metrics Highlight: Focusing on the most critical KPIs and trends, avoiding information overload.
- Visualizations: Utilizing charts, graphs, and other visual elements to present data effectively and highlight key insights.
- Drill-Down Capabilities: Providing the ability to drill down into more detailed data for deeper analysis when needed.
- Regularity and Accessibility: Ensuring reports are generated and distributed regularly (e.g., daily, weekly, monthly, quarterly) and are easily accessible through centralized platforms.
- Actionable Insights: Reports should not just present data but also provide insights and recommendations for action.
Well-designed reports and dashboards enhance transparency, build trust, and demonstrate the value of IT to the organization.
💰12. Financial Planning and Investment
Effective financial planning and strategic investment are critical for the successful execution and sustainability of an IT strategy. This section outlines the processes for budgeting, cost management, and demonstrating the financial value of IT initiatives. It ensures that IT investments are aligned with financial objectives, optimized for return, and managed with fiscal responsibility.
IT Budget Planning and Allocation
IT budget planning is a cyclical process that translates strategic IT objectives into financial terms, allocating resources to support planned initiatives and ongoing operations. Key considerations include:
- Strategic Alignment: Ensuring that budget allocations directly support the strategic IT objectives and, by extension, the overall business goals.
- Zero-Based Budgeting (ZBB) or Activity-Based Costing (ABC): Exploring budgeting methodologies that require justification for all expenses, rather than simply adjusting previous budgets, to ensure efficient resource allocation.
- Capital Expenditure (CapEx) vs. Operational Expenditure (OpEx): Clearly distinguishing between one-time investments (hardware, software licenses, infrastructure build-out) and recurring costs (cloud subscriptions, maintenance, support, personnel).
- Demand Management: Forecasting future IT demands based on business growth, new initiatives, and technological advancements to ensure adequate funding.
- Budget Cycles: Establishing clear annual or multi-year budget cycles with defined timelines for planning, review, and approval.
- Contingency Planning: Allocating a contingency budget to address unforeseen issues, scope changes, or emerging opportunities.
Cost-Benefit Analysis Framework
A robust cost-benefit analysis (CBA) framework is essential for evaluating proposed IT investments and justifying their financial viability. CBA systematically compares the total costs of an initiative with its anticipated benefits. Key elements include:
- Identification of Costs: Including direct costs (hardware, software, licenses, personnel, training), indirect costs (overhead, management time), and intangible costs (disruption, learning curve).
- Identification of Benefits: Quantifying direct benefits (revenue increase, cost savings, efficiency gains) and intangible benefits (improved customer satisfaction, enhanced reputation, better decision-making, increased agility).
- Time Value of Money: Incorporating concepts like Net Present Value (NPV), Internal Rate of Return (IRR), and Payback Period to account for the time value of money and provide a more accurate financial assessment.
- Sensitivity Analysis: Performing analysis to understand how changes in key assumptions (e.g., project duration, benefit realization) impact the financial outcomes.
- Risk Adjustment: Factoring in potential risks and their financial implications into the analysis.
CBA provides a data-driven basis for prioritizing investments and making informed decisions.
ROI Measurement and Tracking
Measuring and tracking the Return on Investment (ROI) of IT initiatives is crucial for demonstrating value, ensuring accountability, and guiding future investment decisions. This involves:
- Baseline Establishment: Defining clear baseline metrics before project initiation to enable accurate measurement of impact.
- Benefit Realization Tracking: Continuously monitoring and quantifying the actual benefits achieved against the projected benefits outlined in the business case.
- Post-Implementation Review: Conducting formal reviews after project completion to assess actual costs and benefits, compare them against initial projections, and identify lessons learned.
- Dashboard and Reporting: Creating dashboards and reports that visually represent the ROI of key IT investments, making it easy for stakeholders to understand the financial impact.
- Continuous Optimization: Using ROI data to identify areas for further optimization, cost reduction, or enhanced benefit realization.
Funding Models and Strategies
Organizations can employ various funding models and strategies to finance their IT initiatives, each with its own advantages and disadvantages:
- Centralized Funding: IT budget is managed centrally, providing greater control and consistency but potentially less responsiveness to specific business unit needs.
- Decentralized Funding: Business units manage their own IT budgets, fostering greater ownership and agility but potentially leading to fragmentation and lack of standardization.
- Chargeback/Showback Models: Charging business units for IT services consumed (chargeback) or showing them the cost of services (showback) to promote accountability and cost awareness.
- OpEx vs. CapEx Optimization: Strategically leveraging cloud services and subscription models to shift from capital-intensive CapEx to more flexible OpEx, improving financial agility.
- Innovation Funds: Dedicated pools of capital for experimental projects, R&D, and emerging technology exploration.
- Partnerships and Joint Ventures: Collaborating with external entities to share costs and risks for strategic IT initiatives.
Financial Risk Management
Managing financial risks associated with IT investments is a critical aspect of financial planning. This includes:
- Budget Overruns: Implementing robust project management and financial controls to prevent cost overruns.
- Underperformance of Investments: Regularly reviewing the performance of IT assets and projects to ensure they are delivering expected value.
- Technology Obsolescence: Planning for the deprecation and replacement of outdated technology to avoid high maintenance costs and security risks.
- Vendor Financial Stability: Assessing the financial health of key IT vendors to mitigate risks of service disruption.
- Cybersecurity Financial Impact: Quantifying the potential financial impact of cyberattacks and data breaches and factoring this into risk mitigation strategies.
By integrating these financial planning and investment practices, the IT strategy can ensure fiscal responsibility, optimize resource utilization, and demonstrate clear financial value to the organization.
🛠️13. Templates and Tools
To facilitate the practical application of this IT Strategy Roadmap, a collection of templates and tools can be utilized. These resources streamline the planning, assessment, implementation, and monitoring processes, ensuring consistency, efficiency, and effectiveness. While specific tools may vary based on organizational preference and existing infrastructure, the following categories represent essential aids for IT strategy development and execution.
Strategic Planning Templates
These templates provide structured formats for documenting key strategic decisions and plans:
- IT Strategy Document Template: A comprehensive template for outlining the entire IT strategy, including executive summary, vision, objectives, initiatives, and governance.
- Technology Roadmap Template: A visual representation of planned technology initiatives over time, showing key milestones, dependencies, and resource requirements.
- Business Case Template: A standardized format for justifying IT investments, detailing costs, benefits, risks, and strategic alignment.
- IT Vision and Mission Statement Template: Guides the articulation of the IT department's purpose and aspirational future state.
- SWOT Analysis Template: A structured grid for identifying and analyzing internal Strengths and Weaknesses, and external Opportunities and Threats related to IT.
Assessment Checklists and Frameworks
These tools aid in systematically evaluating the current state and identifying areas for improvement:
- Current State Assessment Checklist: A detailed checklist covering IT infrastructure, applications, processes, and capabilities to ensure comprehensive evaluation.
- IT Maturity Model Assessment: A framework (e.g., CMMI, COBIT maturity levels) to assess the current maturity of IT processes and identify areas for advancement.
- Risk Assessment Matrix: A tool for categorizing and prioritizing IT risks based on likelihood and impact.
- Vendor Assessment Checklist: A guide for evaluating potential IT vendors based on technical capabilities, financial stability, security, and support.
Implementation Planning Tools
These resources support the detailed planning and execution of IT initiatives:
- Project Charter Template: Defines the project's purpose, objectives, scope, stakeholders, and high-level requirements.
- Work Breakdown Structure (WBS) Template: Breaks down project deliverables into smaller, manageable tasks.
- Gantt Chart Template: A visual tool for scheduling project tasks, showing timelines, dependencies, and progress.
- Change Management Plan Template: Outlines the strategy for managing organizational change, including communication, training, and resistance management.
- Test Plan Template: A structured document for planning and executing various types of IT testing (e.g., unit, integration, UAT).
Monitoring and Reporting Templates
These templates facilitate the tracking of progress and communication of performance:
- KPI Dashboard Template: A visual dashboard for tracking key performance indicators related to IT operations, project progress, and strategic objectives.
- Project Status Report Template: A standardized format for reporting on project progress, issues, risks, and budget status to stakeholders.
- Risk Register Template: A centralized log for tracking identified risks, their mitigation strategies, and current status.
- Service Level Agreement (SLA) Template: Defines performance metrics and service expectations for IT services.
Decision-Making Matrices
These tools aid in structured decision-making processes:
- Prioritization Matrix: A tool for ranking initiatives based on multiple criteria (e.g., impact vs. effort, strategic alignment vs. feasibility).
- RACI Matrix Template: Defines roles and responsibilities (Responsible, Accountable, Consulted, Informed) for tasks and decisions within IT projects.
- Build vs. Buy Analysis Template: A framework for evaluating whether to develop a solution internally or acquire it from an external vendor.
By leveraging these templates and tools, organizations can enhance the rigor, consistency, and efficiency of their IT strategy development and implementation processes, ensuring a more structured and successful approach to technology management.
📚14. Case Studies and Best Practices
Learning from the experiences of others is invaluable in refining an IT strategy. This section provides insights from industry-specific examples, highlights successful implementation stories, and distills common pitfalls and best practices. These real-world applications offer practical guidance and demonstrate the tangible impact of well-executed IT strategies.
Industry-Specific Examples
Different industries face unique challenges and opportunities, influencing their IT strategic priorities. Examining industry-specific case studies can provide tailored insights:
- Healthcare: Focus on interoperability, data security (HIPAA compliance), telehealth platforms, and AI for diagnostics and personalized medicine. Case studies might include hospitals leveraging cloud-based EHR systems for improved patient care or pharmaceutical companies using AI for drug discovery.
- Financial Services: Emphasis on cybersecurity, regulatory compliance (e.g., GDPR, PCI DSS), digital banking platforms, blockchain for secure transactions, and AI for fraud detection and personalized financial advice. Examples could be banks implementing open banking APIs or fintechs utilizing AI for credit scoring.
- Retail: Prioritization of e-commerce platforms, supply chain optimization, customer analytics, in-store technology (e.g., IoT sensors, AR for virtual try-ons), and personalized marketing. Case studies might feature retailers using AI to predict consumer trends or optimizing logistics with advanced analytics.
- Manufacturing: Focus on Industry 4.0 initiatives, IoT for predictive maintenance, automation and robotics, supply chain resilience, and data analytics for operational efficiency. Examples include smart factories using interconnected systems for real-time production monitoring or manufacturers implementing digital twins for product design.
- Government/Public Sector: Emphasis on digital government services, cybersecurity, data privacy, cloud adoption for efficiency, and citizen engagement platforms. Case studies could involve government agencies modernizing legacy systems or implementing secure cloud solutions for public data.
Successful Implementation Stories
Analyzing successful IT strategy implementations provides actionable lessons and inspiration. These stories often highlight:
- Clear Vision and Leadership: The importance of strong executive sponsorship and a well-articulated vision that guides all IT initiatives.
- Business-IT Alignment: How close collaboration between IT and business units led to solutions that directly addressed business needs and delivered measurable value.
- Phased Approach and Agility: The benefits of breaking down large transformations into smaller, manageable phases, allowing for flexibility and adaptation.
- Focus on User Adoption: Strategies employed to ensure end-user buy-in and effective utilization of new systems through comprehensive change management and training.
- Data-Driven Decision Making: How organizations leveraged data and analytics to monitor progress, identify issues, and make informed adjustments throughout the implementation.
- Talent Development: The critical role of investing in IT talent, upskilling existing employees, and attracting new expertise to support strategic objectives.
- Robust Governance: The establishment of effective governance structures that ensured accountability, managed risks, and facilitated timely decision-making.
Lessons Learned and Common Pitfalls
Understanding common challenges and failures can help organizations avoid costly mistakes:
- Lack of Business Alignment: IT initiatives pursued in isolation from business goals often fail to deliver value or gain executive support.
- Inadequate Change Management: Resistance from employees, insufficient training, and poor communication can derail even technically sound implementations.
- Scope Creep: Uncontrolled expansion of project requirements leading to budget overruns, schedule delays, and diluted focus.
- Underestimation of Complexity: Failing to account for the true complexity of integrations, data migration, or legacy system modernization.
- Insufficient Resource Allocation: Underfunding or understaffing critical initiatives, leading to delays, quality issues, or burnout.
- Ignoring Cybersecurity: Treating security as an afterthought rather than an integral part of the strategy, leading to vulnerabilities and breaches.
- Poor Data Quality: Relying on inaccurate or inconsistent data for decision-making, leading to flawed insights and ineffective solutions.
- Lack of Executive Sponsorship: Without strong support from top leadership, IT initiatives may struggle to gain traction and overcome organizational hurdles.
Best Practice Guidelines
Based on successful implementations and lessons learned, the following best practices are recommended for developing and executing an IT strategy:
- Start with Business Strategy: Ensure the IT strategy is a direct enabler of the overall business strategy, not a standalone technical plan.
- Engage Stakeholders Early and Continuously: Involve business leaders, end-users, and other key stakeholders throughout the entire lifecycle of the strategy.
- Conduct a Thorough Current State Assessment: Understand existing capabilities, gaps, and risks before defining the future state.
- Define a Clear Future State Vision: Articulate an aspirational yet achievable vision for how technology will support the organization's future.
- Prioritize Initiatives Strategically: Focus on initiatives that deliver the highest business value and align with strategic objectives.
- Implement Robust Governance: Establish clear decision-making processes, roles, and oversight mechanisms.
- Invest in Change Management: Proactively manage the human side of change through communication, training, and support.
- Embrace Agility and Iteration: Adopt flexible methodologies that allow for adaptation and continuous improvement.
- Prioritize Cybersecurity and Risk Management: Integrate security by design and comprehensive risk management throughout all IT initiatives.
- Measure and Communicate Value: Define clear KPIs, track performance, and regularly communicate the business value delivered by IT.
- Foster a Culture of Innovation: Encourage experimentation, explore emerging technologies, and continuously seek new ways to leverage technology.
- Manage Vendors and Partners Effectively: Build strong relationships and ensure external dependencies contribute positively to the strategy.
By adhering to these guidelines, organizations can significantly increase the likelihood of developing and implementing a successful IT strategy roadmap that drives sustainable business growth and innovation.
15. Appendices
Glossary of Terms
- AI (Artificial Intelligence): The simulation of human intelligence processes by machines, especially computer systems.
- Agile: An iterative and incremental approach to project management and software development.
- API (Application Programming Interface): A set of defined rules that enable different applications to communicate with each other.
- BCDR (Business Continuity and Disaster Recovery): A set of processes and procedures to ensure that critical business functions can continue during and after a disaster.
- CapEx (Capital Expenditure): Funds used by a company to acquire, upgrade, and maintain physical assets such as property, industrial buildings, or equipment.
- CBA (Cost-Benefit Analysis): A systematic process for calculating and comparing the benefits and costs of a project or decision.
- CIO (Chief Information Officer): The senior executive responsible for the information technology and computer systems that support enterprise goals.
- Cloud Computing: The delivery of on-demand computing services—from applications to storage and processing power—typically over the internet and on a pay-as-you-go basis.
- CRM (Customer Relationship Management): A technology for managing all your company’s relationships and interactions with customers and potential customers.
- CTO (Chief Technology Officer): The executive in charge of an organization’s technological needs as well as its research and development (R&D).
- DevOps: A set of practices that combines software development (Dev) and IT operations (Ops) to shorten the systems development life cycle and provide continuous delivery with high software quality.
- DLP (Data Loss Prevention): A set of tools and processes used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users.
- DRP (Disaster Recovery Plan): A documented process or set of procedures to recover and protect a business IT infrastructure in the event of a disaster.
- EHR (Electronic Health Record): A digital version of a patient’s paper chart.
- Endpoint Security: The practice of securing endpoints, such as desktops, laptops, and mobile devices, from cyber threats.
- ERP (Enterprise Resource Planning): A system that integrates all facets of an operation, including product planning, development, manufacturing, sales, and marketing.
- GDPR (General Data Protection Regulation): A legal framework that sets guidelines for the collection and processing of personal information from individuals within the European Union (EU).
- IAM (Identity and Access Management): A framework of policies and technologies to ensure that the right users have the appropriate access to technology resources.
- IoT (Internet of Things): The network of physical objects—'things'—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet.
- ITIL (Information Technology Infrastructure Library): A framework providing best practice guidance for IT service management.
- KPI (Key Performance Indicator): A measurable value that demonstrates how effectively a company is achieving key business objectives.
- ML (Machine Learning): A subset of AI that enables systems to learn from data without being explicitly programmed.
- NIST (National Institute of Standards and Technology): A physical sciences laboratory and a non-regulatory agency of the United States Department of Commerce that promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology.
- NPM (Network Performance Monitoring): The process of measuring and monitoring the quality of service of a computer network.
- OpEx (Operational Expenditure): An ongoing cost for running a product, business, or system.
- PCI DSS (Payment Card Industry Data Security Standard): A set of security standards designed to ensure that all companies that accept, process, store or transmit credit card information maintain a secure environment.
- POC (Proof of Concept): A realization of a certain method or idea to demonstrate its feasibility, or a demonstration in principle with the aim of verifying that some concept or theory has practical potential.
- RPO (Recovery Point Objective): The maximum tolerable period in which data might be lost from an IT service due to a major incident.
- RTO (Recovery Time Objective): The maximum tolerable duration of time within which a business process must be restored after a disaster or disruption.
- SDLC (Software Development Lifecycle): A process used by the software industry to design, develop and test high-quality software.
- SIEM (Security Information and Event Management): A solution that helps organizations detect, analyze, and respond to security threats by combining security information management (SIM) and security event management (SEM) functions.
- SLA (Service Level Agreement): A commitment between a service provider and a client.
- SMART (Specific, Measurable, Achievable, Relevant, Time-bound): A mnemonic used to guide in the setting of objectives.
- SOC (Security Operations Center): A centralized function within an organization that employs people, processes, and technology to continuously monitor and improve an organization's security posture.
- SWOT Analysis: A strategic planning technique used to help an organization identify Strengths, Weaknesses, Opportunities, and Threats related to business competition or project planning.
- TCO (Total Cost of Ownership): A financial estimate of the direct and indirect costs of a product or system.
- TOM (Target Operating Model): A description of the desired future state of an organization, including its processes, people, and technology.
- UAT (User Acceptance Testing): The final phase of software testing where actual users test the software to make sure it can handle required tasks in real-world scenarios.
- VUCA (Volatility, Uncertainty, Complexity, Ambiguity): A mnemonic that describes or reflects on the volatility, uncertainty, complexity and ambiguity of general conditions and situations.
- ZBB (Zero-Based Budgeting): A method of budgeting in which all expenses must be justified for each new period.
Reference Materials and Sources
- [1] Electric AI. (2023, April 6). What is an IT Strategy? Framework & Examples. Retrieved from https://www.electric.ai/blog/guide-to-it-strategy
- [2] CIO Wiki. (2023, August 11). IT Strategy Framework. Retrieved from https://cio-wiki.org/wiki/IT_Strategy_Framework
- [3] Quantive. Top 10 Strategic Planning Frameworks & How to Use Them. Retrieved from https://quantive.com/resources/articles/top-strategic-frameworks
- [4] McKinsey. (2025, July 22). McKinsey technology trends outlook 2025. Retrieved from https://www.mckinsey.com/capabilities/mckinsey-digital/our-insights/the-top-trends-in-tech
12. Financial Planning and Investment
Effective financial planning and strategic investment are critical for the successful execution and sustainability of an IT strategy. This section outlines the processes for budgeting, cost management, and demonstrating the financial value of IT initiatives. It ensures that IT investments are aligned with financial objectives, optimized for return, and managed with fiscal responsibility.
IT Budget Planning and Allocation
IT budget planning is a cyclical process that translates strategic IT objectives into financial terms, allocating resources to support planned initiatives and ongoing operations. Key considerations include:
- Strategic Alignment: Ensuring that budget allocations directly support the strategic IT objectives and, by extension, the overall business goals.
- Zero-Based Budgeting (ZBB) or Activity-Based Costing (ABC): Exploring budgeting methodologies that require justification for all expenses, rather than simply adjusting previous budgets, to ensure efficient resource allocation.
- Capital Expenditure (CapEx) vs. Operational Expenditure (OpEx): Clearly distinguishing between one-time investments (hardware, software licenses, infrastructure build-out) and recurring costs (cloud subscriptions, maintenance, support, personnel).
- Demand Management: Forecasting future IT demands based on business growth, new initiatives, and technological advancements to ensure adequate funding.
- Budget Cycles: Establishing clear annual or multi-year budget cycles with defined timelines for planning, review, and approval.
- Contingency Planning: Allocating a contingency budget to address unforeseen issues, scope changes, or emerging opportunities.
Cost-Benefit Analysis Framework
A robust cost-benefit analysis (CBA) framework is essential for evaluating proposed IT investments and justifying their financial viability. CBA systematically compares the total costs of an initiative with its anticipated benefits. Key elements include:
- Identification of Costs: Including direct costs (hardware, software, licenses, personnel, training), indirect costs (overhead, management time), and intangible costs (disruption, learning curve).
- Identification of Benefits: Quantifying direct benefits (revenue increase, cost savings, efficiency gains) and intangible benefits (improved customer satisfaction, enhanced reputation, better decision-making, increased agility).
- Time Value of Money: Incorporating concepts like Net Present Value (NPV), Internal Rate of Return (IRR), and Payback Period to account for the time value of money and provide a more accurate financial assessment.
- Sensitivity Analysis: Performing analysis to understand how changes in key assumptions (e.g., project duration, benefit realization) impact the financial outcomes.
- Risk Adjustment: Factoring in potential risks and their financial implications into the analysis.
CBA provides a data-driven basis for prioritizing investments and making informed decisions.
ROI Measurement and Tracking
Measuring and tracking the Return on Investment (ROI) of IT initiatives is crucial for demonstrating value, ensuring accountability, and guiding future investment decisions. This involves:
- Baseline Establishment: Defining clear baseline metrics before project initiation to enable accurate measurement of impact.
- Benefit Realization Tracking: Continuously monitoring and quantifying the actual benefits achieved against the projected benefits outlined in the business case.
- Post-Implementation Review: Conducting formal reviews after project completion to assess actual costs and benefits, compare them against initial projections, and identify lessons learned.
- Dashboard and Reporting: Creating dashboards and reports that visually represent the ROI of key IT investments, making it easy for stakeholders to understand the financial impact.
- Continuous Optimization: Using ROI data to identify areas for further optimization, cost reduction, or enhanced benefit realization.
Funding Models and Strategies
Organizations can employ various funding models and strategies to finance their IT initiatives, each with its own advantages and disadvantages:
- Centralized Funding: IT budget is managed centrally, providing greater control and consistency but potentially less responsiveness to specific business unit needs.
- Decentralized Funding: Business units manage their own IT budgets, fostering greater ownership and agility but potentially leading to fragmentation and lack of standardization.
- Chargeback/Showback Models: Charging business units for IT services consumed (chargeback) or showing them the cost of services (showback) to promote accountability and cost awareness.
- OpEx vs. CapEx Optimization: Strategically leveraging cloud services and subscription models to shift from capital-intensive CapEx to more flexible OpEx, improving financial agility.
- Innovation Funds: Dedicated pools of capital for experimental projects, R&D, and emerging technology exploration.
- Partnerships and Joint Ventures: Collaborating with external entities to share costs and risks for strategic IT initiatives.
Financial Risk Management
Managing financial risks associated with IT investments is a critical aspect of financial planning. This includes:
- Budget Overruns: Implementing robust project management and financial controls to prevent cost overruns.
- Underperformance of Investments: Regularly reviewing the performance of IT assets and projects to ensure they are delivering expected value.
- Technology Obsolescence: Planning for the deprecation and replacement of outdated technology to avoid high maintenance costs and security risks.
- Vendor Financial Stability: Assessing the financial health of key IT vendors to mitigate risks of service disruption.
- Cybersecurity Financial Impact: Quantifying the potential financial impact of cyberattacks and data breaches and factoring this into risk mitigation strategies.
13. Templates and Tools
To facilitate the practical application of this IT Strategy Roadmap, a collection of templates and tools can be utilized. These resources streamline the planning, assessment, implementation, and monitoring processes, ensuring consistency, efficiency, and effectiveness. While specific tools may vary based on organizational preference and existing infrastructure, the following categories represent essential aids for IT strategy development and execution.
Strategic Planning Templates
These templates provide structured formats for documenting key strategic decisions and plans:
- IT Strategy Document Template: A comprehensive template for outlining the entire IT strategy, including executive summary, vision, objectives, initiatives, and governance.
- Technology Roadmap Template: A visual representation of planned technology initiatives over time, showing key milestones, dependencies, and resource requirements.
- Business Case Template: A standardized format for justifying IT investments, detailing costs, benefits, risks, and strategic alignment.
- IT Vision and Mission Statement Template: Guides the articulation of the IT department\'s purpose and aspirational future state.
- SWOT Analysis Template: A structured grid for identifying and analyzing internal Strengths and Weaknesses, and external Opportunities and Threats related to IT.
Assessment Checklists and Frameworks
These tools aid in systematically evaluating the current state and identifying areas for improvement:
- Current State Assessment Checklist: A detailed checklist covering IT infrastructure, applications, processes, and capabilities to ensure comprehensive evaluation.
- IT Maturity Model Assessment: A framework (e.g., CMMI, COBIT maturity levels) to assess the current maturity of IT processes and identify areas for advancement.
- Risk Assessment Matrix: A tool for categorizing and prioritizing IT risks based on likelihood and impact.
- Vendor Assessment Checklist: A guide for evaluating potential IT vendors based on technical capabilities, financial stability, security, and support.
Implementation Planning Tools
These resources support the detailed planning and execution of IT initiatives:
- Project Charter Template: Defines the project\'s purpose, objectives, scope, stakeholders, and high-level requirements.
- Work Breakdown Structure (WBS) Template: Breaks down project deliverables into smaller, manageable tasks.
- Gantt Chart Template: A visual tool for scheduling project tasks, showing timelines, dependencies, and progress.
- Change Management Plan Template: Outlines the strategy for managing organizational change, including communication, training, and resistance management.
- Test Plan Template: A structured document for planning and executing various types of IT testing (e.g., unit, integration, UAT).
Monitoring and Reporting Templates
These templates facilitate the tracking of progress and communication of performance:
- KPI Dashboard Template: A visual dashboard for tracking key performance indicators related to IT operations, project progress, and strategic objectives.
- Project Status Report Template: A standardized format for reporting on project progress, issues, risks, and budget status to stakeholders.
- Risk Register Template: A centralized log for tracking identified risks, their mitigation strategies, and current status.
- Service Level Agreement (SLA) Template: Defines performance metrics and service expectations for IT services.
Decision-Making Matrices
These tools aid in structured decision-making processes:
- Technology Selection Matrix: A weighted scoring model for evaluating and comparing different technology options against predefined criteria.
- Priority Matrix: A tool for prioritizing IT initiatives based on factors such as business impact, urgency, cost, and resource requirements.
- Make vs. Buy Analysis: A framework for deciding whether to develop solutions internally or purchase from external vendors.
- Risk vs. Reward Matrix: A visual tool for plotting initiatives based on their potential risk and expected returns.
By leveraging these templates and tools, organizations can enhance the rigor, consistency, and efficiency of their IT strategy development and implementation processes, ensuring a more structured and successful approach to technology management.
IT Strategy Framework Diagram
Below is a visual representation of the core components and their interrelationships within an IT Strategy Framework:
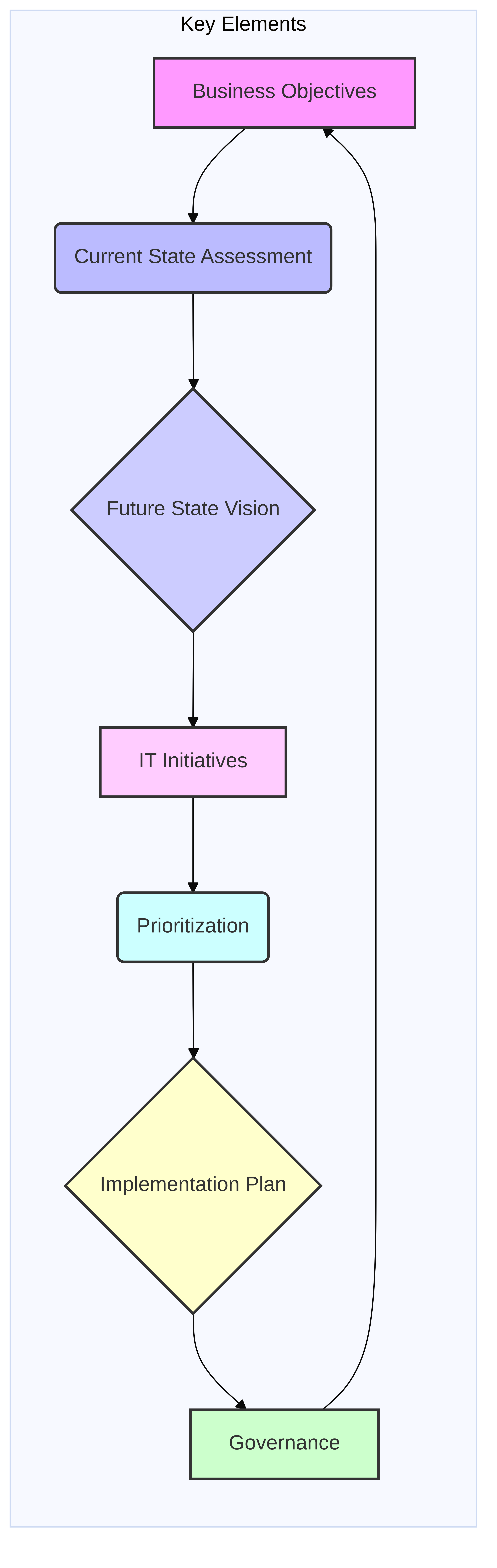
This diagram illustrates the cyclical and interconnected nature of IT strategy development, where each component feeds into the next, creating a continuous improvement loop that ensures the IT strategy remains aligned with business objectives and adapts to changing requirements.
SWOT Analysis Diagram
Below is a visual representation of the SWOT Analysis framework used in IT strategic planning:
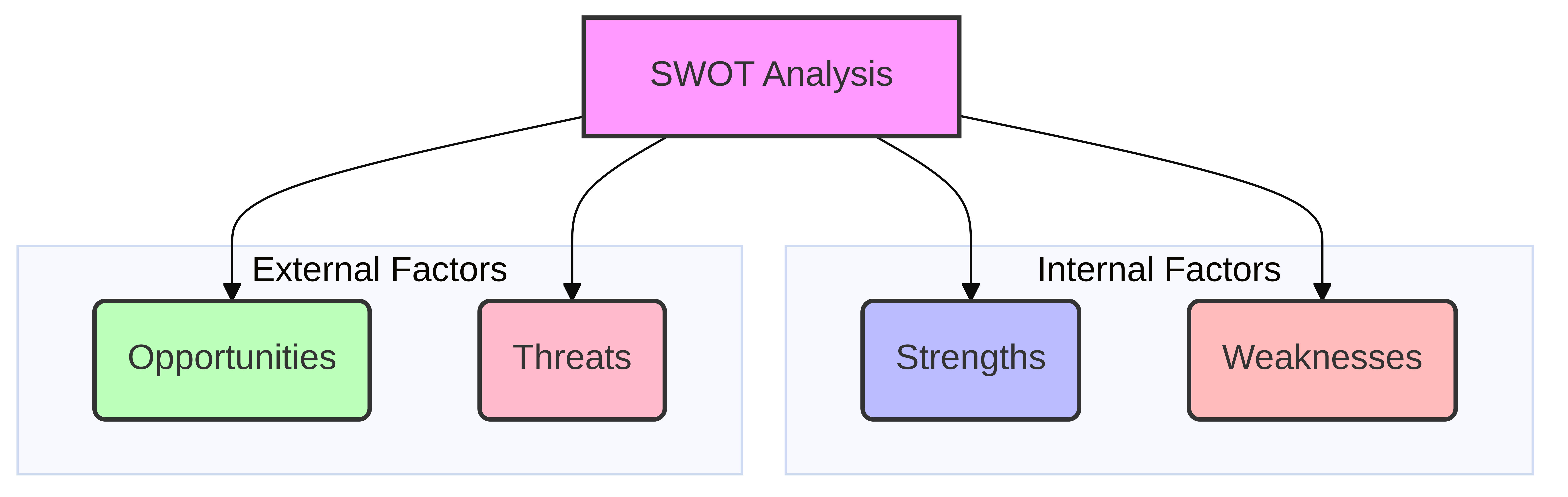
This framework helps organizations systematically analyze their internal capabilities (Strengths and Weaknesses) alongside external environmental factors (Opportunities and Threats) to inform strategic IT decision-making and identify areas for competitive advantage.